Threat Intelligence Response Unit
Zero Trust EDR
Protecting all endpoints , including servers, desktops, laptops, wireless devices, mobile devices and other OT/IoT devices connected to the network from cyber threats.
Secure your Data & Assets with
Threat Intelligence Response Unit (ThIRU).


Monitor – Isolate – Protect
Real-time alerting & reporting
Alerts and reports, based on recent and ongoing events, stop data loss and theft before it happens.
SIEM Integration
Organizations can gain a more holistic view of their security posture, improve threat detection and response times, and comply with regulatory requirements.
Multiple Deployment Options
Appliance, Virtual Machine, Cloud and SaaS options available
AI & ML
Extreme analytics and MI based learning for future proofing.
Deep learning and Forensics
Deep learning capabilities, for the automation of some Digital Forensics Investigation aspects.
Attack Pathways
Visualise cyber attacks with the MITRE ATT&CK framework
Next Generation Cyber Security
Artificial Intelligence and Machine Learning, along with Zero Trust Security. ThIRU EDR establishes trust across the five pillars of Zero Trust architecture to provide visibility and analytics.
Prevent endpoints, in depth
Secure your Windows, macOS, and Linux systems. Stop ransomware before data is encrypted, and block malware. Disrupt advanced threats with behavior-based prevention. Leverage protections from ThIRU EDR.
Enhance visibility of endpoints
Collect data from every major OS, and aggregate logs and alerts from numerous host security and IT tools. Monitor host activity (in the context of your holistic attack surface) with turnkey integrations and dashboards.
Detect in high fidelity
Generate actionable alerts by continuously correlating host activity with broader environmental data. Initiate hunts from anomalies spotted by prebuilt machine learning jobs. Prepare for threats tailoring attacks against organizations like yours.
Respond rapidly
Empower analysts with embedded context, interactive visualizations, and a familiar terminal-like view for investigations. Gather further details with host risk analysis, network packet analysis, and OS-query host inspection.
One agent, many use cases
Disrupt threats, collect telemetry, and take action, all with one agent. Tackle new use cases like DevOps, activating features with just one click. Deploy its small footprint far and wide.
Attack lookback pathways
ThIRU EDR enables users to analyze attack pathways from end to end according to MITRE ATT@CK framework, appreciably improving your security posture.
Device Trust
✓Device Helath✓Scanning & Inventory
✓Malware & Ransomware blocking
✓USB block
✓ Registry management
User Trust
✓Provides strong authentication and dynamic conditional access✓Login and device wise monitoring
✓MFA
✓Only when you need access
Network Trust
✓Network monitoring, traffic, packets & bandwidth✓ Connectivity type monitoring (LAN, WiFI etc
✓Network mapping
Applications
✓Application run time monitoring✓Processes/Application whitelisting
✓ Mail scanning
✓ Browser protection
Attack Pathways
✓By machine✓By user
✓By type
✓By time
✓By threat
Simple Pricing

- Extended detection and response
- Host security analysis
- Network security analysis
- User security analysis
- Timeline event explorer
- Case management
- Detection engine
- Prebuilt detection rules
- Detection alert external actions
- Machine learning anomaly detection
- Prebuilt anomaly detection jobs
- Malware prevention
- Admin-defined endpoint blocklist
- Ransomware prevention
- Malicious behavior protection
- Memory threat protection
- Interactive response console
- Threat Intelligence Platform (TIP)
- Cust. endpoint protection notifications
- CIS posture findings and dashboards
- Workload session auditing
- Virus Protection
Essential protection
Essentials
Basic cyber security protection.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- Pricing
Popular
Essentials+
Mid level cyber security protection.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- Pricing
Ultimate Protection
Enterprise
Ultimate cyber security protection.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- Pricing
Educational.
Educational
Educational cyber security protection.
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- Pricing
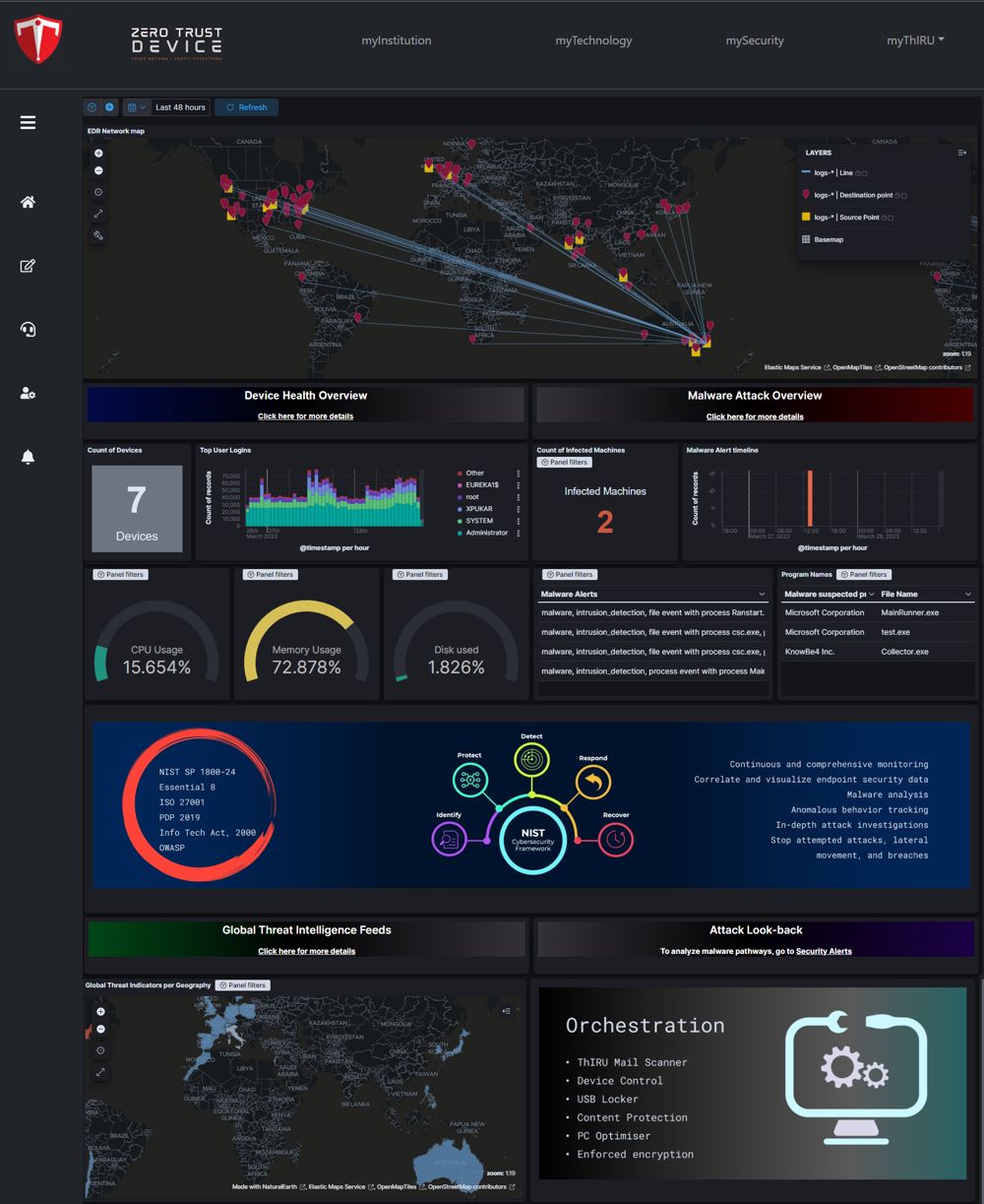
Unified Dashboard easy to operatesecure & Intelligentsingle pane of glass view
To determine the risks in operating assets by connecting business processes and outcomes to business cyber risk and business decision making in a fragmented and crowded complex deployment of technology architectures.